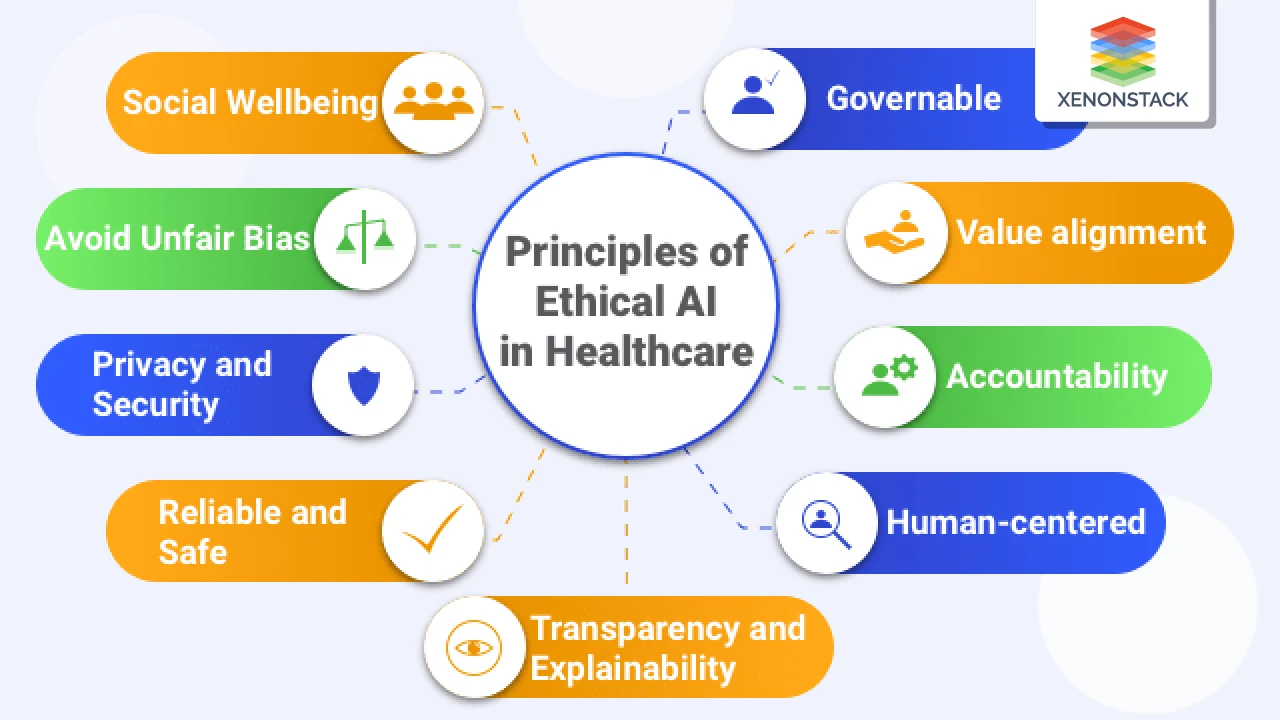
AI and the Future of Cybersecurity Threats and Solutions
Examine the evolving landscape of cybersecurity with AI both as a threat and a defense mechanism.
AI and the Future of Cybersecurity Threats and Solutions
Hey everyone! Let's dive deep into something super critical for our digital lives: cybersecurity. And guess what's shaking things up big time in this space? Yep, Artificial Intelligence. AI isn't just for cool chatbots or generating art anymore; it's becoming a major player in both attacking and defending our online world. It's a bit of a double-edged sword, right? On one hand, AI can be an incredible shield, helping us spot and stop threats faster than ever. On the other, malicious actors are also getting their hands on AI, making their attacks more sophisticated and harder to detect. So, let's break down what this means for you, your business, and the future of staying safe online.
The AI Cybersecurity Landscape Understanding the Battlefield
Think of cybersecurity as a constant battle between good guys and bad guys. For years, it's been a cat-and-mouse game, with defenders trying to keep up with ever-evolving threats. Now, AI is like giving both the cat and the mouse superpowers. This means the stakes are higher, and the game is moving much faster. We're talking about threats that can learn, adapt, and even anticipate defenses. But on the flip side, our defenses can also learn, adapt, and predict attacks. It's a fascinating, albeit sometimes scary, new era.
AI as a Threat The Dark Side of Intelligent Attacks
Let's start with the scary part: how cybercriminals are leveraging AI. They're not just sending out generic phishing emails anymore. AI allows them to craft highly personalized and convincing attacks. Here's how:
- Advanced Phishing and Social Engineering: Imagine an email that sounds exactly like your boss, your bank, or even a family member, asking for sensitive information. AI can analyze vast amounts of public data to create incredibly convincing spear-phishing attacks. It can mimic writing styles, understand organizational structures, and even generate realistic voice deepfakes for vishing (voice phishing) attacks.
- Automated Malware Generation: Traditional malware often relies on known signatures. AI can generate polymorphic malware that constantly changes its code, making it incredibly difficult for traditional antivirus software to detect. It can also create self-modifying ransomware that adapts to its environment to evade detection and maximize damage.
- Intelligent Reconnaissance and Exploitation: AI can autonomously scan networks for vulnerabilities, identify weak points, and even develop custom exploits. This means attackers can find and exploit weaknesses much faster and more efficiently than ever before, often without human intervention.
- Deepfake-Powered Disinformation Campaigns: Beyond financial fraud, AI-generated deepfakes (audio and video) can be used to spread misinformation, manipulate public opinion, or even damage reputations. This is a huge concern for national security and corporate integrity.
- Evasion of AI Defenses: The ultimate challenge is when attackers use AI to understand and bypass AI-powered defenses. This creates an AI-on-AI battle, where the most sophisticated AI wins.
AI as a Solution The Bright Side of Intelligent Defense
Okay, now for the good news! AI is also our most powerful weapon in the fight against these advanced threats. Cybersecurity companies and internal security teams are rapidly adopting AI to bolster their defenses. Here's how AI is becoming our digital guardian:
- Threat Detection and Anomaly Detection: This is where AI truly shines. Traditional security systems rely on predefined rules and signatures. AI, especially machine learning, can analyze massive datasets of network traffic, user behavior, and system logs to identify subtle anomalies that indicate a potential threat. It can spot unusual login patterns, strange data transfers, or never-before-seen malware variants in real-time.
- Automated Incident Response: Once a threat is detected, every second counts. AI can automate parts of the incident response process, such as isolating infected systems, blocking malicious IP addresses, or even rolling back system changes. This significantly reduces the time attackers have to cause damage.
- Vulnerability Management and Patch Prioritization: AI can help organizations understand their attack surface better. It can analyze vulnerabilities, prioritize which ones to patch first based on risk and exploitability, and even predict where new vulnerabilities might emerge.
- User and Entity Behavior Analytics (UEBA): AI-powered UEBA tools build a baseline of normal behavior for every user and device on a network. If an employee suddenly tries to access sensitive files they never have before, or logs in from an unusual location, the AI flags it as suspicious, even if it uses legitimate credentials.
- Security Orchestration Automation and Response (SOAR): AI is a core component of SOAR platforms, which integrate various security tools and automate workflows. This allows security teams to respond to threats more efficiently and consistently, reducing manual effort and human error.
- Predictive Security Analytics: AI can analyze historical attack data and global threat intelligence to predict future attack vectors and prepare defenses proactively. It's like having a crystal ball for cybersecurity.
Key AI-Powered Cybersecurity Products and Solutions
Alright, let's get down to some concrete examples. Many companies are integrating AI into their cybersecurity offerings. Here are a few types of products and some specific examples, along with their use cases, comparisons, and general pricing considerations. Keep in mind, pricing for enterprise-level cybersecurity solutions can vary wildly based on the size of your organization, the number of endpoints, and the specific features you need. Most offer custom quotes.
Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR)
These are crucial for protecting individual devices (endpoints) like laptops, desktops, and servers. XDR takes it a step further by integrating data from endpoints, networks, cloud environments, and email for a more holistic view.
-
Product: CrowdStrike Falcon Insight XDR
- Use Case: Real-time threat detection, prevention, and response across endpoints, cloud workloads, identity, and data. It uses AI to analyze behavioral patterns and identify sophisticated attacks like ransomware and fileless malware.
- Comparison: Known for its lightweight agent, cloud-native architecture, and strong focus on behavioral AI. Often compared to SentinelOne and Microsoft Defender for Endpoint.
- Pricing: Subscription-based, typically per endpoint per year. Can range from $10-$50+ per endpoint annually, depending on modules and volume. Enterprise pricing is custom.
-
Product: SentinelOne Singularity Platform
- Use Case: Autonomous AI-powered endpoint protection, detection, and response. It can automatically remediate threats without human intervention, even offline.
- Comparison: Emphasizes autonomous capabilities and rollback features. Often seen as a direct competitor to CrowdStrike.
- Pricing: Similar subscription model to CrowdStrike, with varying tiers.
-
Product: Microsoft Defender for Endpoint (part of Microsoft 365 Defender)
- Use Case: Comprehensive endpoint security for Windows, macOS, Linux, Android, and iOS. Leverages Microsoft's vast threat intelligence and AI capabilities.
- Comparison: Excellent for organizations already heavily invested in the Microsoft ecosystem. Integrates seamlessly with other Microsoft security products.
- Pricing: Included in higher-tier Microsoft 365 E5 licenses or available as a standalone subscription.
Security Information and Event Management (SIEM) and Security Orchestration Automation and Response (SOAR)
These platforms collect and analyze security logs from across an entire IT environment (SIEM) and then automate responses to detected threats (SOAR).
-
Product: Splunk Enterprise Security (ES)
- Use Case: A leading SIEM solution that uses machine learning to detect advanced threats, perform security investigations, and manage compliance. It ingests massive amounts of data for analysis.
- Comparison: Very powerful and flexible, but can be complex and resource-intensive. Often compared to IBM QRadar and Microsoft Sentinel.
- Pricing: Based on data ingestion volume (GB per day). Can be very expensive for large organizations, ranging from tens of thousands to millions annually.
-
Product: IBM QRadar SIEM
- Use Case: Collects, normalizes, and analyzes log and flow data to detect threats and provide security intelligence. Incorporates AI for anomaly detection and risk scoring.
- Comparison: Strong in network anomaly detection and compliance reporting.
- Pricing: Similar to Splunk, based on data volume and event per second (EPS).
-
Product: Microsoft Sentinel (Cloud-Native SIEM/SOAR)
- Use Case: A scalable, cloud-native SIEM and SOAR solution built on Azure. Uses AI and machine learning for threat detection, investigation, and automated response.
- Comparison: Highly integrated with Azure and Microsoft 365 services. Cost-effective for cloud-first organizations.
- Pricing: Consumption-based, primarily on data ingestion and retention. Can be more flexible than traditional on-premise SIEMs.
-
Product: Palo Alto Networks Cortex XSOAR
- Use Case: A comprehensive SOAR platform that automates security operations, incident response, and threat intelligence management. It uses AI to prioritize alerts and suggest playbooks.
- Comparison: Focuses heavily on automation and orchestration across various security tools.
- Pricing: Enterprise-level, custom quotes.
Network Detection and Response (NDR)
NDR solutions use AI to monitor network traffic for suspicious behavior and anomalies that indicate an attack.
-
Product: Vectra AI Cognito Detect and Respond
- Use Case: AI-driven network detection and response that identifies hidden attackers in real-time across cloud, data center, and enterprise networks. Focuses on detecting attacker behaviors.
- Comparison: Known for its ability to detect sophisticated, stealthy attacks that bypass traditional perimeter defenses.
- Pricing: Enterprise-level, custom quotes.
-
Product: Darktrace Enterprise Immune System
- Use Case: Uses unsupervised machine learning to learn the 'normal' behavior of every user, device, and network segment, then detects subtle deviations that indicate a threat.
- Comparison: Pioneered the 'immune system' approach to cybersecurity.
- Pricing: Enterprise-level, custom quotes.
Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platforms (CWPP)
As more businesses move to the cloud, AI is critical for securing these dynamic environments.
-
Product: Wiz
- Use Case: Provides a unified view of cloud security risks across AWS, Azure, GCP, and Kubernetes. Uses AI to identify critical attack paths and misconfigurations.
- Comparison: Rapidly gained popularity for its agentless approach and comprehensive cloud visibility.
- Pricing: Enterprise-level, custom quotes.
-
Product: Palo Alto Networks Prisma Cloud
- Use Case: Comprehensive cloud-native security platform covering CSPM, CWPP, CIEM (Cloud Infrastructure Entitlement Management), and more. Uses AI for threat detection and compliance.
- Comparison: A broad, integrated platform for multi-cloud security.
- Pricing: Enterprise-level, custom quotes.
Challenges and Considerations The Road Ahead
While AI offers incredible promise for cybersecurity, it's not a magic bullet. There are significant challenges we need to address:
- Data Quality and Bias: AI models are only as good as the data they're trained on. If the data is biased or incomplete, the AI can make incorrect decisions or miss threats.
- Adversarial AI: Attackers are actively working on techniques to fool AI models (e.g., by subtly altering malware to bypass AI detection). This is an ongoing arms race.
- Complexity and Explainability: Some advanced AI models (like deep neural networks) can be black boxes, making it hard to understand why they made a particular decision. This 'explainability' is crucial in cybersecurity for investigations and compliance.
- Talent Gap: We need more cybersecurity professionals who understand both AI and security to effectively deploy, manage, and interpret these advanced systems.
- Cost: Implementing and maintaining sophisticated AI-powered cybersecurity solutions can be expensive, especially for smaller businesses.
- Over-reliance: While AI automates many tasks, human oversight and expertise remain critical. AI should augment, not replace, human security analysts.
Preparing for the AI-Powered Cybersecurity Future Your Action Plan
So, what can you do to stay ahead in this evolving landscape? Whether you're an individual, a small business owner, or part of a large enterprise, here are some actionable steps:
- Embrace AI-Powered Security Tools: Don't stick to outdated defenses. Invest in EDR/XDR, SIEM/SOAR, and NDR solutions that leverage AI for advanced threat detection and automated response.
- Prioritize Data Hygiene: Ensure your data is clean, accurate, and well-managed. This is foundational for effective AI security.
- Train Your Team: Educate your employees about AI-powered social engineering threats (like deepfake phishing) and how to spot them. Also, invest in training for your security team on how to work with and optimize AI tools.
- Stay Informed: The cybersecurity landscape changes daily. Follow industry news, attend webinars, and keep up with the latest threats and AI advancements.
- Implement a Multi-Layered Defense: No single tool, even AI-powered, is foolproof. Combine AI solutions with traditional security measures like strong passwords, multi-factor authentication (MFA), regular backups, and network segmentation.
- Focus on Proactive Security: Don't just react to attacks. Use AI for predictive analytics, vulnerability management, and threat intelligence to anticipate and prevent breaches.
- Consider Managed Security Services (MSSP): If you don't have the in-house expertise or resources, consider partnering with an MSSP that specializes in AI-driven security. They can provide 24/7 monitoring and response.
The future of cybersecurity is undeniably intertwined with AI. It's a race, and both sides are getting smarter. By understanding the threats and proactively adopting AI-powered solutions, we can significantly strengthen our defenses and navigate the complex digital world with greater confidence. Stay safe out there!
:max_bytes(150000):strip_icc()/277019-baked-pork-chops-with-cream-of-mushroom-soup-DDMFS-beauty-4x3-BG-7505-5762b731cf30447d9cbbbbbf387beafa.jpg)